Few months ago, I had a conversation with a sister from my place of worship, and it was one of the exciting conversations I have had in recent times and I will tell you why.
Not to go into much details, she and her team are working on a mind blowing project and I asked how it was going. Prior to this project,they had picked one but I was very excited about the new one they picked. So while we were talking,she seem to have a concern about her project and I suggested CONDITIONAL ACCESS and explained what it does and how it can serve her project. I felt so proud of myself after that conversation.
So, I will give y'all a scenrio where you can use CONDITIONAL ACCESS.
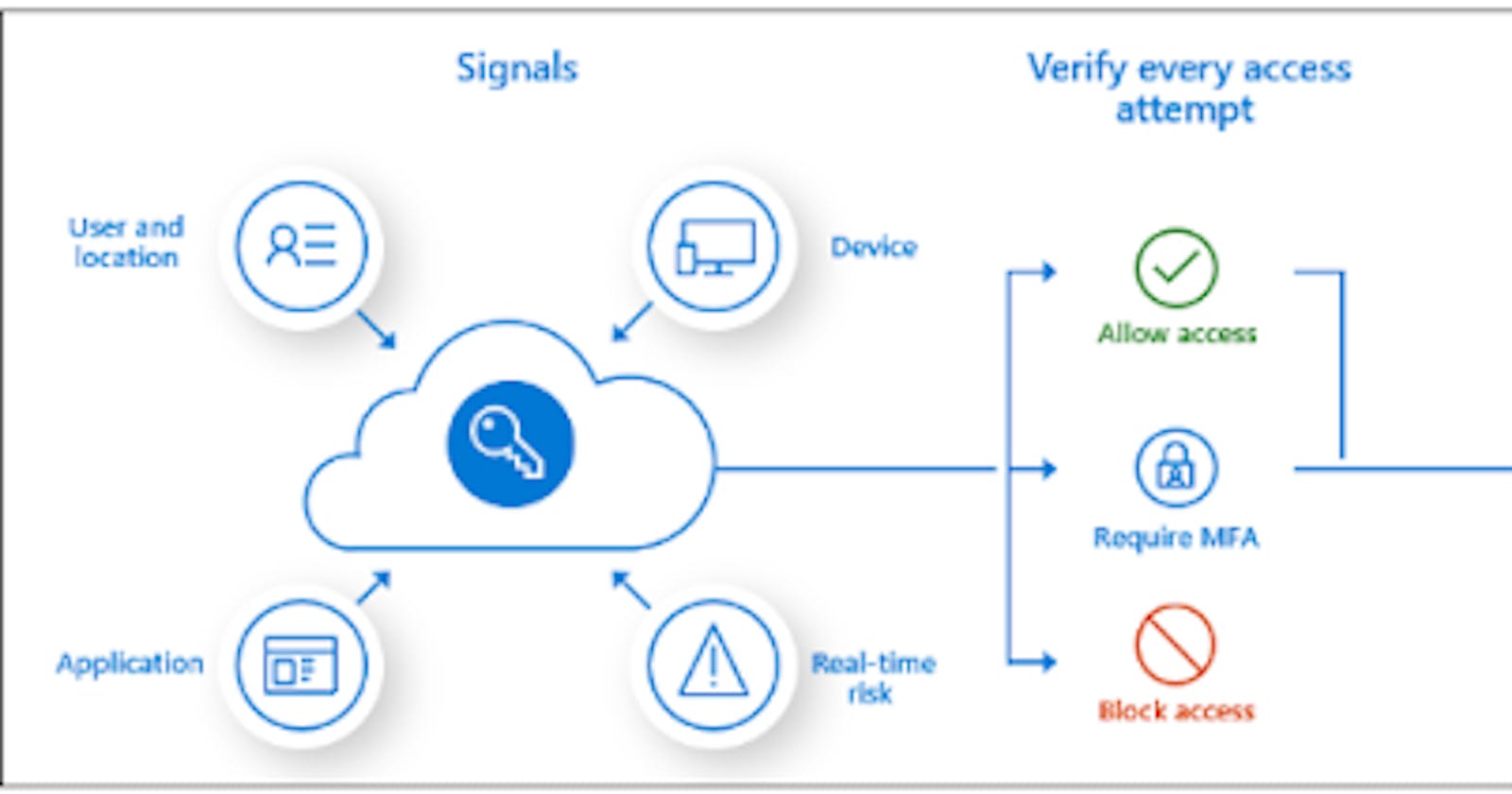
Let's say you run a company and employees working for your company are to access a software or something. You most likely will give them a laptop or a device to be able to do this. This device is called a MANAGED DEVICE cos you configured it to work within the scope of what it is supposed to do for you. In this case,they can hardly use it for personal use. The CONDITIONAL ACCESS could help the employee access things from anywhere (which the administrator can configure to be within a location). The employees will need some Multi Factor Authorization (MFA) to sign in and authenticate their identites so the organisation is sure they are the ones signing in(they could even use work designated email for this purpose). In addtion, the IP address which the device was configured is only recognized so you can't be using thier personal laptop to run work stuff,you get?
This is perfect for Hybrid workers, and remote workers. Onsite workers can use this also if they have all the devices at the office configured.
The advantage of this to the company is that it helps to protect the organization's assets. Before all configurations made to access company's workspace or software can be compromised, you will get a signal as an administrator managing this access. Note that it doesn't defend or block denial-of-service (DoS) attacks, but it can send you signals from these events to determine whether you should grant access outside of the policies and protection already set.
If your organisation has been thinking of a way to manage access to sensitive stuff or company's stuff in general,you should suggest CONDITIONAL ACCESS to them.
This can also service entreprenuers in a different way but I will be giving out too much information already. 😉
Does your company or organisation use something like this? or have you seen a similar scenrio? Now you know what it is called☺️ . Do you care to share?